Security Enhanced Anonymous Two Factor Mutual Authentication Scheme with Key Agreement
Copyright ⓒ 2018 The Digital Contents Society
This is an Open Access article distributed under the terms of the Creative Commons Attribution Non-CommercialLicense(http://creativecommons.org/licenses/by-nc/3.0/) which permits unrestricted non-commercial use, distribution, and reproduction in any medium, provided the original work is properly cited.

Abstract
Various researcher study two-factor authentication schemes for the session initiation protocol for enhancing security, it is reason that password-based authentication schemes have security limitation on off-line password attack. Lu et al. suggested two-factor authentication scheme. it uses elliptic curve cryptography and provides the anonymity and key agreement for session initiation protocol but has security problems. Reddy et al. found out Lu et al.’ scheme’s vulnerability and proposed an enhanced anonymous two-factor mutual authentication with key-agreement scheme for session initiation protocol. However, their scheme has security vulnerability, so this paper executes the operation process analysis of Reddy et al.’ authentication scheme. This paper proposed the security enhanced anonymous two factor mutual authentication scheme with key agreement scheme to protecting off-line password guessing attack, DoS attack, wrong password change phase, and session key disclosure attack using biometrics’s fuzzy extraction.
초록
세션 개시 프로토콜의 보안성을 향상시키고, 패스워드 기반의 기법들은 일반적으로 오프라인 패스워드 공격에 취약하다는 특징을 해결하기 위해서 두 가지 요소 상호 인증 기법에 대한 연구를 진행하고 있다. Lu 등은 타원곡선 암호를 기반으로 한 익명성과 키 동의를 제공하는 세션 게시 프로토콜을 두 가지 요소 인증 기법으로 제안하였지만, 몇 가지 보안상의 문제점이 있었다. Reddy 등은 Lu 등이 제안한 기법의 문제점을 지적하고 보다 보안성이 향상되고 익명성이 보장되는 두 가지 요소 상호 인증 기법을 제안하였다. Reddy 등이 제안한 인증 기법에도 다양한 보안 취약점이 발견되었다. 본 논문에서 Reddy 등이 제안한 기법의 동작과정을 분석하고 안전한 인증기법을 제안하고자 한다. 제안하는 인증 기법은 Reddy 등이 제안한 기법에서 발견된 오프라인 패스워드 추측 공격, DoS 공격, 잘못된 패스워드 변경, 세션키 노출 공격 등을 포함한 다양한 보안 문제점을 퍼지 추출 기술을 활용하여 해결하였다. 본 논문에서 제안하는 기법은 기존의 기법보다 보안성이 향상되고 키 동의를 제공하며 익명성이 보장되는 두 가지 요소 상호인증 기법이다.
Keywords:
Security analysis, Session initiation protocol, User authentication scheme키워드:
안전성 분석, 세션 개시 프로토콜, 사용자 인증 기법Ⅰ. Introduction
Session Initiation Protocol(known as SIP) is the important communications scheme to control multimedia communication sessions. SIP is a text-based protocol, incorporating various elements of the hypertext transfer protocol and the simple mail transfer protocol. SIP can alter, establish and terminate the connection between various communication parties. SIP is made for application layer protocol and it is designed to be independent of the underlying transport layer.[1]
SIP is involved for the signaling operations of communication session and is primarily used to set up and terminate voice or video calls. SIP can use to establish two-party or the multi-party sessions. And SIP is text- based protocol. It is used for requests from clients and responses from the servers over the public communication. Rosenberg et al. proposed the authentication scheme using SIP with challenge -response protocol in 2002. Various studies show more efficient and secure authentication schemes for SIP after Rosenberg et al.’s scheme proposed.[2]
Lu et al. proposed anonymous two-factor based authenticated key agreement scheme using elliptic curve cryptography for SIP.[3] They shows security analysis on various against attacks and provides anonymity. But Reddy et al. found out that Lu et al.’ scheme has weak problems on imperfect mutual authentication and extraction of sensitive information, and in not secure to user impersonation attacks. And Reddy et al. proposed security enhanced elliptic curve cryptography based scheme. Their scheme provide anonymous two-factor mutual user authentication with key agreement scheme for SIP. Reddy et al. shows security analysis on the mutual authentication, user anonymity, perfect forward secrecy and is more secure on various attacks than various authentication schemes including Lu et al.’s scheme.[4] In this paper, first paper analyze authentication phases of Reddy et al.’ authentication scheme. And Reddy et al.’ scheme have security vulnerabilities such as off-line password guessing attack, a DoS attack, wrong password change phase, and session key disclosure attack. And then, this paper propose security enhanced authentication scheme.
This paper is organized as follows. Section 2 reviews the Reddy et al.’s authentication scheme. Section 3 analyzes the vulnerabilities regard as security problem in Reddy et al.’s authentication scheme. Section 4 proposes security enhanced authentication scheme, and section 5 executes security analysis on proposed scheme including the Lu et al. and Reddy et al.’ authentication scheme. Section 6 concludes the paper.
Ⅱ. Review of Reddy et al.’s Scheme
This section reviewed Reddy et al.’s scheme of the registration and authentication phase.[4, 5] Notations of this paper are listed the Table 1.
In the system initialization phase of Reddy et al.’ scheme, Before the protocol is ever executed, Reddy et al.’ scheme computes and shares the secret. S generates a point P on an elliptic curve E(a, b) over Fp. S selects h(∙) and PriS , and calculates PubS = PriS ∙ P. S stores PriS and publishes { E(a, b), P, PubS, h(∙) }.
2-1 User registration phase
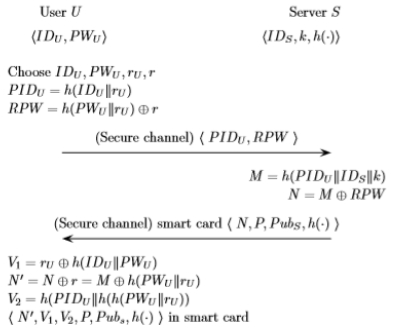
This phase is performed once when user U registers with the server. User U selects IDU, PWU, and two random numbers rU and r. And then smart catd computes PIDU = h ( IDU || rU ), RPW = h ( PWU || rU )⊕ r. And U sends the registration request { IDU , RPW } to S using a further secure communication. Server S computes M, N as follows. M = h ( PIDU || IDS || k ), N = M ⊕ RPW. And then, server S puts {N, P, PubS , h(∙) } on user U’s smart card SC and send it to U. user U computes V1, N', V2 as follows. V1= rU ⊕ h ( IDU || PWU ), N′ = Nr = M ⊕ h ( PWU || rU ), V2 = h ( PIDU || h ( PWU || rU )), And then, the U stores them on the received SC. SC includes the values {N′, V1, V2, P, PubS , h (∙)}. Figure 1 shows user registration phase of Reddy et al.’s Scheme.
2-2 Key agreement authentication phase
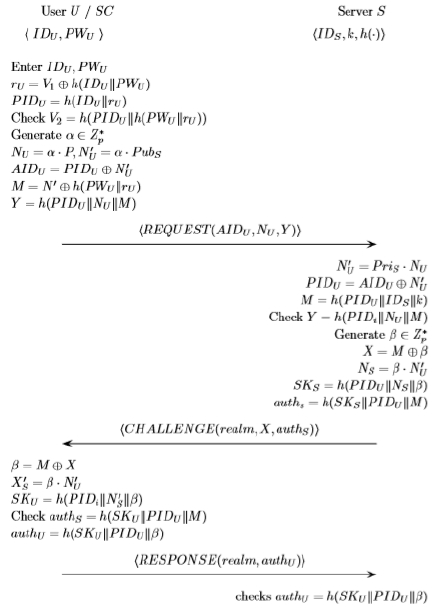
Figure 2 shows Key agreement authentication phase of Reddy et al.’s scheme. User U and server S can authenticate each other and compute a session key in mutual authentication with key agreement. U inputs smart card SC and inputs own IDU and PWU. SC computes rU, PIDU. rU = V1 ⊕ h (IDU ||PWU ), PIDU = h ( IDU || rU ), and checks the accuracy V2 ⊕ h ( PIDU || h ( PWU || rU )).
If they are same, then the smart card SC generates a random number α and computes NU, M , Y as follows. NU = a∙ P , N`U = a∙ PubS, M = N′⊕ h (PWU || rU), Y = h(PIDU || NU || M ), And then, user U sends the REQUEST( AIDU , NU , Y ) to server S. S computes N`U , PIDU , M as follows. N`U = PriS ∙ NU , PIDU = AIDU ⊕ N`U, M = h ( PIDU ||IDS || k ), And then, verifies Y = h ( PIDU ||NU|| M ).
If they are same, server S authenticates U. if not, process stops. S generates a random number β and calculate X, NS, SKS, authS. X = M⊕β, NS = β ∙ N`U, SKS = h ( PIDU || NS || β ), authS = h ( SKS || PIDU || M ), And then, server S sends CHALLENGE(realm, X, authS ) to user U. Then using receiving CHALLENGE messages, SC computes β, N`S , SKU as follows. β = M ⊕ X , N`S = β ∙ N`U, SKU = h ( PIDU || N`S || β), And then, the server S verifies authS messages as follows. authS = h ( SKU || PIDU || M ). If authS is same to h ( SKU || PIDU || M ), U authenticates S and further computes authU. authU = h ( SKU || PIDU || β ), And then, U sends the RESPONSE( realm, authU ) to server S. Server S checks authU = h ( SKS|| PIDU || β ). If they are same, S accepts for next communication using computed session key SKU = SKS. If not, S drops the session key and stop the communication with U.
SKU = h ( PIDU || N`S || β ),
SKS = h ( PIDU || NS || β ).
2-3 Password changing phase
Reddy et al.’s protocol claims that users can freely update user’s passwords. The password change phase works as follows. U inserts SC and enters the existing user’s IDU and PWU. SC computes rU. rU=V1⊕h(IDU||PWU). And SC checks calculated value and V2 as follows. V2 = h( PIDU|| h(PWU|| rU)). If V2 = h(PIDU|| h ( PWU || rU )) are corresponding, then U derives M as follows. M=N′⊕ h(PWU||rU). A user U selects a new password PWUnew and computes RPWnew, V1new, N′new, V2new as follows. RPWnew=h (PWUnew||rU)⊕r, V1new= rU ⊕ h ( IDU||PWUnew), N′new=M⊕h(PWUnew||rU), V2new =h (PIDU || h(PWUnew||rU)). Then, S replaces existing values on the received SC. Thus, SC contains {N′new, V1new, V2new, P, PubS, h(∙)}.
Ⅲ. Security Problem on Reddy et al.’s
This paper found out that Reddy et al.’ scheme have security vulnerabilities such as off-line password guessing attack, a DoS attack, wrong password change phase, session key disclosure.
3-1 Off-line Password Guessing Attack
An attacker can reveal user’s identity and password from user’s smart card in Reddy et al.’s authentication scheme. the attacker can analyze the stored information of smart card using the simple power analysis or differential power analysis.[7-9] If the attacker steals the user’s smart card, and then the attacker obtains the all of information {N’, V1, V2, P, Pubs, h(∙)} from smart card using physical monitoring. So the attacker can knows formula of all parameters such as V2, PIDU and rU.
V2 = h ( PIDU || h ( PWU||rU), PIDU = h⊕(IDU||rU), rU = V1⊕ h(IDU||PWU).
The attacker can compute V2=h(PIDU|| h(PWU ||rU) as follows. Using PIDU → V2=h (h(IDU ||rU)||h( PWU||rU), Using rU → V2 = h(h(IDU|| V1⊕h(IDU||PWU))||h(PWU||V1 h(IDU||PWU)).
The attacker got V1, V2, h(∙) from U’s SC, and so does not know IDU and PWU on V2 = h(h(IDU ||V1⊕h(IDU||PWU))||h(PWU||V1⊕h(IDU|| PWU)). The attacker can guess the IDU and PWU because they are both small size. |Did| and |Dpw| defined the number of identities in Did and the number of passwords in Dpw. If TH is the running time for hash funtion, the running time of the aforementioned attack procedure is |Did| * |Dpw| * TH), because both PW and ID are human-memorable short strings but not high-entropy keys. So |Did| and |Dpw| are often chosen from two corresponding dictionaries of small size. As |Did| and |Dpw| are very limited in practice, |Did|≤ |Dpw| ≤ 106, the aforementioned attack can be completed inpolynomial time. Therefore the attacker can IDU and PWU using off-line password (and identity) guessing attack on Reddy et al.’s authentication scheme.
3-2 DoS Attack
Reddy et al.’s scheme has problem on A DoS attack. Their scheme use random number for preventing the replay attack but does not use timestamp so the scheme is weak on DoS. The attacker can obtain and intercept the previous authentication message {AIDU, NU and Y} in the public communication. The attacker sends { AIDU, NU and Y} again after authentication phase ends. But the server cannot found out that the message is previous message and cannot checks the legitimacy of incoming message because the server cannot check and know the freshness of message before authU is same to h(SKS||PIDU||β). So the server executes various operation such as generating the random number operation, ∙ operation, hash operation, and exclusive OR operations before checking whether the attacker’s authU and computed h (SKS||PIDU||β) are same. so the attacker can execute the DoS attack without difficulty.[7-9]
3-3 Wrong password change phase
Reddy et al.’s authentication scheme has procedural problem. If an user changes own password, first the user inputs IDU and PWU. So, the user’s SC computes rU , M and verifies V2 as follows. rU=V1⊕h(IDU||PWU), V2=h(PIDU ||h(PWU||rU)), M = N′⊕ h ( PWU || rU).
And the user chooses a new password PWUnew and have to compute RPWnew as follows. RPWnew = h (PWUnew || rU ) ⊕ r. But the user cannot compute RPWnew because the user does not know parameter r. parameter r does not store in the smart card and cannot compute r using other parameters. A parameter related r in smart card is only N’ as follows.
N = N ⊕ r , N = M ⊕ RPWN = h (PIDU ||IDS || k ) ⊕ h(PWU || rU) ⊕ r→ N′= h(PIDU ||IDS||k)⊕h(PWU||rU ⊕ r ⊕ r→ N′= h( PIDU||IDS || k )⊕ h ( PWU || rU )
N’ does not contain the information about r because the parameter r is removed by ⊕ operation. So the user of Reddy et al.’s scheme cannot change the user’s password because user cannot calculate parameter r.
3.4 Session key disclosure attack
An attacker can calculate the session key SK including previous session key using SK. Reddy et al.’s authentication scheme is weak on session key disclosure attack. An attacker can obtains all of AID, X including previous AID, X in public communication In this scheme, Using an power analysis, an attacker found out user’s smart card, the attacker can extracts all information from the smart card. And he can compute user’s IDU and PWU using the stored information. So he has AID, X, IDU, PWU, N’, and V1, so he can calculate the session key.
rU = V1h ( IDU || PWU ),
PIDU = h (IDU || rU ) [ using computed rU ],
N`U = AIDU⊕PIDU [using computed PIDU ],
M = N′⊕ h(PWU ||rU) [using computed rU],
β = MX [using computed M ],
NS = β ∙ N`U [using computed β ]
→ SKU = h ( PIDU || N`S || β )
The attacker computes all formula's parameter of session key SKU = h (PIDU || N`S || β ). It is important that the attacker can computes all of session key including previous session key.
Ⅳ. Security enhanced authentication scheme
This section proposes an improved anonymous two-factor authentication with key-agreement for session initiation protocol using elliptic curve cryptography based various studies.[10-20]
4-1 System initialization phase
Before the protocol is ever executed, this scheme computes and shares the secret.
(1) S generates a point P on an elliptic curve E(a, b) over Fp.
(2) S selects h(∙) and PriS , and calculates PubS = PriS ∙ P.
(3) S stores PriS and publishes {E(a, b), P, PubS, h(∙) }.
4-2 User registration phase
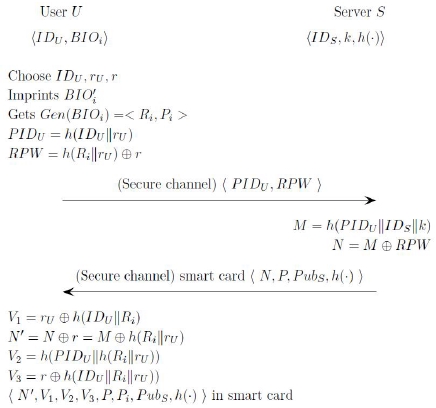
For a user U, this phase is executed once when User U registers itself with the server.
(1) User U selects IDU and two random numbers rU and r. Then U imprints biometrics BIOi and Generate Ri, Pi and PIDU, RPW.
Gen(BIOi’) = < Ri , Pi > ,
PIDU = h ( IDU || rU ) , RPW = h ( PWU || rU )⊕r
And U sends registration request { IDU , RPW } to S using a secure communication.
(2) S calculates M, N as follows;
M = h ( PIDU || IDS || k ), N = M⊕RPW
And then, S inputs { N, P, PubS , h(∙) } on user’s smart card SC and send it to U .
(3) U computed V1 , N′, V2, V3 as follows.
V1= rU⊕ h(IDU|| PWU,
N′= N ⊕ r = M ⊕ h (PWU || rU),
V2 = h(PIDU|| h(PWU|| rU )),
V3 = r ⊕ h( IDU || Ri || rU ))
And then, U stores them on the received smart card SC. Therefore SC(Smart Card) stores { N , V1 ,V2 , V3 , P, Pi , PubS , h (∙)}. Figure 3 shows user registration phase of proposed scheme.
4-3 Key agreement authentication phase
This paper proposed secure authentication scheme with key-agreement phase, user U and server S can authenticate each other and the they compute a session-key of them. Figure 4 shows the process of authentication phase.
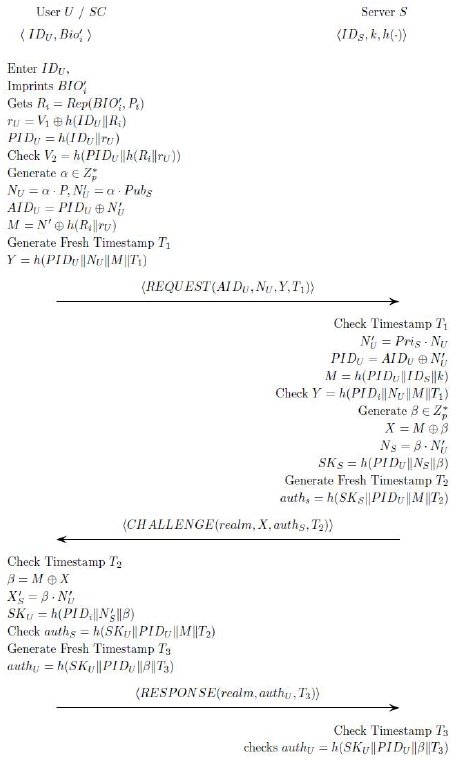
(1) U inserts SC and enters IDU and imprint BIOi. Then SC computes Ri, rU, and PIDU .
Ri = Rep(BIO’i, Pi), rU = V1 ⊕ h ( IDU || PWU ) , PIDU = h ( IDU || rU ). And checks the accuracy of V2 . V2 = h ( PIDU || h ( PWU || rU )). And then the SC generates a random number α and computes NU, AIDU, timestamp T1, M , Y as follows;
NU = a ∙ P , N`U = a∙ PubS , AIDU = PIDU ⊕ N`U, M = N′⊕ h (PWU || rU), Y = h (PIDU || NU || M || U). User U sends the REQUEST( AIDU, NU, Y, T1 ) to server S.
(2) S checks the received timestamp T1, and calculates N`U , PIDU, M. N`U = PriS ∙NU , PIDU = AIDU ⊕N`U, M = h( PIDU ||IDS || k ).
And then, verifies Y = h ( PIDU ||NU|| M|| T1). If they are not same, process aborts. S generates a random number β and computes X, NS, SKS, authS , S’s timestamp T2. X = M⊕β , NS = β ∙ N`U , SKS = h( PIDU || NS || β ), Generate T2, authS = h (SKS|| PIDU || M ||T2).
S sends CHALLENGE(realm, X, authS, T2) to U.
(3) U receives CHALLENGE messages, SC checks timestamps T2 and computes β, N`S, SKU.
β = M ⊕ X, N`S =β∙N`U, SKU= h (PIDU || N`S || β )And then checks authS messages as follows;
authS = h ( SKU || PIDU || M || T2 )
If authS is same to h ( SKU||PIDU||M|| T2 ), U generates T3 and computes authU. authU = h ( SKU || PIDU || β || T3 ). And then, U sends the RESPONSE(realm, authU ) to server S.
(4) S checks T3 and authU = h ( SKS|| PIDU || β ). If they are same, S computed session key SKU = SKS for using next communication.
4-4 Biometrics updating phase
Proposed scheme allows users to freely update biometrics on biometrics updating phase as shown in Figure 5.
(1) U inserts SC and enters the own user’s IDU and imprint BIO’i. SC computes Ri, rU, r as follows ; Ri = Rep(BIO’i, Pi ), rU = V1 ⊕ h ( IDU || Ri), r = V3 ⊕ h(IDU || Ri || rU )). And then, SC verifies the computed value and V2 as follows; V2 = h( PIDU || h (Ri || rU )). If V2 = h( PIDU || h ( Ri || rU )) are same, then U imprint new BIOi , generate new Rinew and Pinew and compute M = N′⊕ h( Rinew|| rU).
(2) U computes RPWnew, V1new, V2new, V3new, , N′new as follows; RPWnew = h (Rinew|| rU )⊕r,
V1new = rU ⊕ h ( IDU || Rinew ),
N′new = M ⊕ h ( Rinew || rU ),
V2new = h ( PIDU || h ( Rinew||rU )),
V3new = r ⊕ h(IDU || Rinew || rU)).
And then, user U replaces the existing values on the smart card as follows.
{N′new, V1new, V2new, P , Pinew , PubS , h(∙)}.
Ⅴ. Security analysis of Proposed scheme
This paper compares the security analysis on Lu et al., Reddy et al., and the proposed scheme. Table 2 shows the security analysis comparison as follows.
Reddy et al. execute security analysis and a proposed the enhanced anonymous two-factor mutual authentication with key-agreement scheme for session initiation protocol. Lu et al.‘s scheme is secure DoS attack and provide secure password change phase. But Reddy et al. ’s scheme is provide ①, ②, ③, ④ but have important security problems on ⑤, ⑥, ⑦, ⑧ as mentioned this paper. The proposed scheme is secure and providing the user anonymity, mutual authentication, protect sensitive information, impersonation attack, off-line password guessing attack, DoS attack, secure password change phase, session key disclosure attack using the biometrics BIOi, V3 and timestamp T. And proposed scheme changes the values of Y, authU, authS due to protecting DoS attack. The biometrics using fuzzy extraction BIOi, Ri, Pi provides the security probability on off-line password guessing attack, session key disclosure attack.
Ⅵ. Conclusion.
This paper discussed possible attacks for Reddy et al.'s authentication scheme, and a modified scheme was proposed to improve security and protect against various attacks such as off-line password guessing attack, DoS attack, secure password change phase, session key disclosure attack. This scheme was security enhanced anonymous two factor mutual authentication scheme with key agreement more than other scheme.
Acknowledgments
This work was supported by the National Research Foundation of Korea grant funded by Korea government (Ministry of Science, ICT & Future Planning) (NRF-2017R1C1B5017492) and this research was supported by financial support of Howon University in 2018.
References
- Johnston, Alan, "SIP: understanding the session initiation protocol, Artech House", Inc., Norwood, (2003).
- Rosenberg, Jonathan, et al., SIP: session initiation protocol, No. RFC 3261, (2002).
-
Lu, Yanrong, et al., "An anonymous two-factor authenticated key agreement scheme for session initiation protocol using elliptic curve cryptography", Multimedia Tools and Applications, 76(2), p1801-1815, (2007).
[https://doi.org/10.1007/s11042-015-3166-4]

-
Reddy, Alavalapati Goutham, et al., "An enhanced anonymous two-factor mutual authentication with key-agreement scheme for session initiation protocol", Proceedings of the 9th International Conference on Security of Information and Networks, ACM, (2016).
[https://doi.org/10.1145/2947626.2947650]

- He, Debiao, Jianhua Chen, and Yitao Chen, "A secure mutual authentication scheme for session initiation protocol using elliptic curve cryptography", Security and Communication Networks, p1423-1429, (2012).
-
Ma, Chun‐Guang, Ding Wang, and Sen‐Dong Zhao, "Security flaws in two improved remote user authentication schemes using smart cards", International Journal of Communication Systems, 27(10), (2014).
[https://doi.org/10.1002/dac.2468]

-
Choi, Younsung, et al., "Security enhanced anonymous multiserver authenticated key agreement scheme using smart cards and biometrics", The Scientific World Journal, (2014).
[https://doi.org/10.1155/2014/281305]

- Choi, Younsung, "Cryptanalysis on Anonymous Two Factor Mutual Authentication with Key Agreement Scheme For Session Initiation Protocol", Research Journal of Applied Sciences, 12(5), (2017).
-
He, Debiao, and Sherali Zeadally, "An analysis of rfid authentication schemes for internet of things in healthcare environment using elliptic curve cryptography", IEEE internet of things journal, 2(1), (2015).
[https://doi.org/10.1109/jiot.2014.2360121]

-
Chaudhry, Shehzad Ashraf, et al., "A secure and efficient authenticated encryption for electronic payment systems using elliptic curve cryptography", Electronic Commerce Research, 16(1), p113-139, (2016).
[https://doi.org/10.1007/s10660-015-9192-5]

-
Chaudhry, Shehzad Ashraf, "An improved and secure biometric authentication scheme for telecare medicine information systems based on elliptic curve cryptography", Journal of Medical Systems, 39(11), (2015).
[https://doi.org/10.1007/s10916-015-0335-y]

-
Reddy, Alavalapati Goutham, et al., "A secure anonymous authentication protocol for mobile services on elliptic curve cryptography", IEEE Access, 4, (2016).
[https://doi.org/10.1109/access.2016.2596292]

-
Choi, Younsung, et al., "Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography", Sensors, 14(6), (2014).
[https://doi.org/10.3390/s140610081]

-
Farash, Mohammad Sabzinejad, Saru Kumari, and Majid Bakhtiari, "Cryptanalysis and improvement of a robust smart card secured authentication scheme on SIP using elliptic curve cryptography", Multimedia Tools and Applications, 75(8), p4485-4504, (2016).
[https://doi.org/10.1007/s11042-015-2487-7]

-
Choi, Younsung, Youngsook Lee, and Dongho Won, "Security improvement on biometric based authentication scheme for wireless sensor networks using fuzzy extraction", International Journal of Distributed Sensor Networks, 12(1), (2016).
[https://doi.org/10.1155/2016/8572410]

-
Madhusudhan, R., and R. C. Mittal, "An efficient fingerprint-based remote user authentication protocol using mobile devices", Proceedings of the International Conference on Soft Computing for Problem Solving, (SocProS 2011) December 20-22, 2011, Springer, India, (2012).
[https://doi.org/10.1007/978-81-322-0491-6_52]

-
Kumari, Saru, Muhammad Khurram Khan, and Rahul Kumar, "Cryptanalysis and improvement of ‘a privacy enhanced scheme for telecare medical information systems’", Journal of medical systems, 37(4), (2013).
[https://doi.org/10.1007/s10916-013-9952-5]

-
Li, Xiong, et al., "Robust dynamic ID–based remote user authentication scheme using smart cards", International journal of ad hoc and ubiquitous computing, 17(4), (2014).
[https://doi.org/10.1504/ijahuc.2014.066423]

- H. J. Yang, D. H. Kim, and Y. G. Seo, “Noise-robust Hand R egion Segmentation In RGB Color-based Real-time Image”, The Journal of Digital Contents Society, 18(8), p1603-1613, Dec), (2017.
-
K. H. Park, and H. S. Noh, “Effective Acne Detection using Component Image a* of CIE L*a*b* Color Space”, Journal of Digital Contents Society, 19(7), p1397-1403, July), (2018.
[https://doi.org/10.9728/dcs.2018.19.7.1397]

저자소개

2006.2 : Sungkyunkwan University, Information and Communication Engineering (B.S Degree
2007.8 : Sungkyunkwan University, Department of Electrical and Computer Engineering(M.S Degree)
2015.8 : Sungkyunkwan University, Department of Electrical and Computer Engineering(Ph.D Degree)
2010.6~2013.5 : Department of Information engineering, Korea Army Academy at Yeong-Cheon, Assistant professor
2016.3~now: Major of Cyber Security, Division of Computer, Howon University, Assistant professor
※Research Interests : Information security, Digital forensics, Cloud security