Hop-based Aggressive Caching Scheme for Hybrid Mobile Ad-hoc Networks
Copyright ⓒ 2018 The Digital Contents Society
This is an Open Access article distributed under the terms of the Creative Commons Attribution Non-CommercialLicense(http://creativecommons.org/licenses/by-nc/3.0/) which permits unrestricted non-commercial use, distribution, and reproduction in any medium, provided the original work is properly cited.

Abstract
Hybrid mobile ad hoc networks are networks that combine the Internet with mobile ad hoc networks. In the wireless transmission scheme, nodes located within the transmission range of each other can receive the transmitted content irrespective of destination. The caching technique stores such received content and uses it for future requests. This paper proposes an aggressive caching scheme based on the number of transport hops. In the proposed scheme, the service request and provision is made along the tree path with the AP as the root node. The node caches the received content based on its own hop count. When the routing process is completed, the node becomes a path node responsible for transmission or an adjacent node of the path node without any extra process. Simulation results show that the proposed caching scheme can achieve better performance compared to conventional aggressive caching scheme.
초록
하이브리드 모바일 에드 혹 네트워크는 인터넷을 모바일 애드 혹 네트워크와 결합한 네트워크이다. 무선 전송 방식에서, 서로의 전송 범위 내에 위치하는 전송 된 콘텐트를 목적지 여부와는 무관하게 수신 할 수 있다. 캐싱 기술은 이러한 수신 된 콘텐트를 저장하고 차후 발생되는 요청에 사용된다. 본 논문에서는 전송 홉 수에 기반한 적극적 캐싱 기법을 제안한다. 제안 된 기법에서, 서비스 요청 및 제공은 AP를 루트 노드로 하는 트리 경로를 따라 이루어진다. 노드는 자신의 홉 수에 따라 수신 된 콘텐트를 캐시한다. 라우팅 프로세스가 완료되면, 노드는 추가적인 처리 과정 없이 전송 또는 인접 노드를 담당하는 경로 노드로 설정된다. 시뮬레이션 결과는 제안 된 캐싱 기법이 기존의 적극적 캐싱 기법에 비해 더 나은 성능을 달성 할 수 있음을 보여준다.
Keywords:
Caching, Hybrid Mobile Ad-hoc Networks, MANETs, Multimedia, Streaming Service키워드:
캐싱, 하이브리드 모바일 에드 혹 네트워크, 마넷, 멀티미디어, 스트리밍 서비스Ⅰ. Hop-based Aggressive Caching Scheme
This paper proposes a cooperative caching scheme based on the number of node’s hops, Hc. We assume the following network environment for the proposed caching technique. A sufficient number of nodes subsist in the network to avoid black hole problem due to node movement. AP acts as a gateway between the Internet and the node. The AP executes the proactive method of performing the route setting every predetermined time Tr. The network topology is a tree structure with the AP as the root. The node does not broadcast the service request packet. This packet is forwarded only between the route nodes and delivered to the AP. The proxy performs the role of storing and providing the transmitted content [1]. The proxy is selected from the path node and the neighboring node according to the relationship with the transmission path. A path node is a node that constitutes a transmission route between a server and a requesting node. The neighboring node is a node located within the transmission range of the route node.
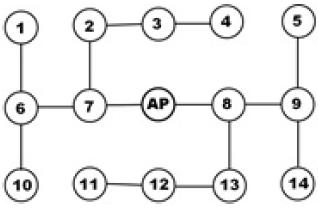
Fig. 1. shows an example of a network topology at time t. The solid lines represent the links between the nodes. Assume that node 14 requests multimedia content Mi at time t. The node refers to its own routing table and sends a request packet to the parent node, node 9, to connect with the AP. The node 9 receiving the request packet transmits the packet to the parent node 8, in the same way mentioned above. The request packet sent by node 14 passes through nodes 9 and 8, which are ancestor nodes of node 14, and finally to the AP. The content Mi sent by the AP is delivered to the node 14 along the reverse path to which the request packet was forwarded. MANETs [2] use the store-and-forward transport scheme, so path nodes 8 and 9 store content Mi. Node 7 is neighbor node of the AP. In the proposed scheme, this node caches content Mi that is sent to node 14. In the next step, node 13, neighbor node of node 8, caches content Mi. When node 9 transmits content Mi, neighbor node 5 of node 9 caches it. Thus, content Mi is stored in node 14 as a local cache and in node 8 and 9 as a path cache, and in node 5, 7 and 13 as an adjacent cache.
In this paper, the node decides whether or not the received data is cached based on its own hop count, Hc, from the server. If Hc is 0, the node performs caching regardless of its own hop value. The caching process mentioned above has Hc value of zero. The hop value of the AP is 1. If Hc is 2, content Mi is stored in local cache 14, path cache 3 and 9, and adjacent cache 7. If Hc is 3, content Mi is stored in local cache 14, path cache 3 and 9, and adjacent cache 7 and 13.
The cache hit ratio is the sum of cache hit ratio of the local cache, the route cache, and the adjacent cache. Let P(l), P(p), and P(a) be the probability of cache hit of local cache, path cache and adjacent cache, respectively.
| (1) |
where Pc is the probability of caching content and N(a) is the mean number of neighboring nodes per path node, respectively.
Ⅱ. Simulation
This section shows the simulation results for analyzing the performance of the proposed caching scheme. The simulation environment is as follows. The size of network is 800 m ⅹ 800 m square plane. To ensure of full connectivity, the number of node is 100. Multimedia content Mi has 30 seconds playing time. The number of contents is 100 and their popularities are defined according to the zipf like distribution with 0.85 skew factor [3]. Node mobility is defined as random waypoint (RWP) where maximum speed is 8 km/s and pause time is 5 seconds [4].
Cache replacement algorithm is LRU [5]. The simulation execution time is 10000 seconds. The rest simulation parameters are shown in Table. 1.
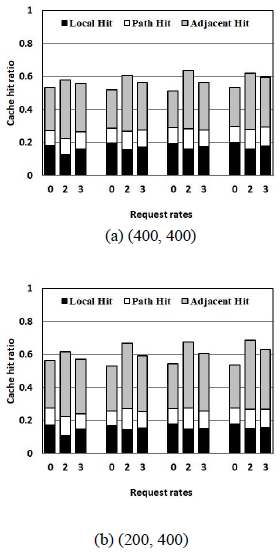
In the initial state, the nodes are situated at arbitrarily selected coordinates in the network. The nodes move freely over time using the mobility defined in the RWP. Fig. 2 shows the cache hit ratios when the number of hops (Hc) to select a proxy node to perform caching is 0, 2, and 3. The x-axis represents the request rate. If the value of Hc is 0, all neighbor nodes perform caching. When Hc is 2, the nodes located within the transmission range of AP, all nodes capable of direct link establishment, are selected as the proxy. When Hc is 3, a proxy is selected from the neighbor nodes of AP and the child nodes of AP toward the request node. Fig. 2 shows the highest cache hit ratio when the HC value is 2. The simulation results show that the cache hit ratio decreases as the Hc value increases. The cache size of a node is relatively small compared to the total amount of content the server provides. As the Hc value increases, the probability of being selected as a proxy increases. As a result, content stored in the node cache is often replaced with up-to-date incoming content.
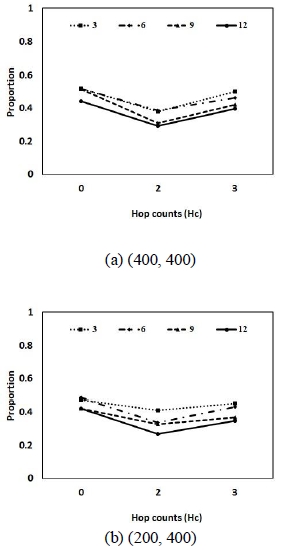
Fig. 3 shows the ratio of transport channels when using caching techniques according to various request rates. The Y-axis represents the ratio of the number of transmission channels to whether caching is used or not. The simulation results show that the number of channels for transmission is reduced most when all nodes adjacent to the AP, Hc = 2, perform caching. The simulation results show that the cache hit ratio and transmission efficiency can be achieved as the cache update frequency is lower for multimedia data.
Ⅲ. Conclusion
In MANETs, nodes handle all the processes involved in communication themselves. The caching scheme allows the requested content to be served from the node closer to the requesting node than from the server. The use of caching technology enables efficient use of transmission bandwidth and node energy. In this paper, we propose a hop-based caching scheme using aggressive method. Proxies that perform caching are naturally chosen in the routing process, so there is no need for additional processing for selecting them. In order to evaluate the performance of the proposed scheme, simulation was performed in terms of cache hit ratio and transmission channel reduction proportion at various request rates. From the simulation results, the proposed scheme can achieve better cache hit ratio and transmission efficiency than the aggressive caching scheme.
References
-
P. Srivastava, and R. Kumar, “An efficient proxy adaptive gateway discovery algorithm based on quality of service parameters”, International Journal of Communication Networks and Distributed Systems, 16(3), p261-280, (2016).
[https://doi.org/10.1504/ijcnds.2016.076653]

- S. Lee, J. Kim, and J. Park, "An Efficient Protection Scheme against Distributed DoS Attacks in VANET using Bloom Filter", The Journal of Digital Contents Society, 18(6), p1157-1163, Oct), (2017.
-
Y. Ma, and A. Jamalipour, “A cooperative cache-based content delivery framework for intermittently connected mobile ad hoc networks”, IEEE Transactions on Wireless Communications, 9(1), p366-373, (2010).
[https://doi.org/10.1109/twc.2010.01.090775]

-
P. Nayak, and P. Sinha, “ Analysis of Random Way Point and Random Walk Mobility Model for Reactive Routing Protocols for MANET Using NetSim Simulator”, Artificial Intelligence, Modelling and Simulation (AIMS), IEEE, p427-432, (2015).
[https://doi.org/10.1109/aims.2015.87]

-
N. Laoutaris, H. Che, and I. Stavrakakis, “The LCD interconnection of LRU caches and its analysis”, Performance Evaluation, 63(7), p609-634, (2006).
[https://doi.org/10.1016/j.peva.2005.05.003]

저자소개

2001 : MS of Information and Telecommunication Engineering, Incheon National University
2006 : Ph.D. of Information and Telecommunication Engineering, Incheon National University
1993~1997 : Samsung Electronics
2013~2016 : Visiting Professor at Incheon National University
※Research interests: QoS, distributed multimedia system, wireless access network, and MobileAd-hocNetwork

1983 : Seoul National Unversity, MS.
1990 : New Jersey Institute of Technology, MS
1994 : George Mason University, Ph.D.
1983~1985: Samsung Electronics, R&D Staff
1990~1995: GMU CS/CfIA Research Assistant and Associate
1995~1996: Electronics and Telecommunications Research Institute, Computing Division Research Staff
1996~Current: Catholic University of Korea, Professor of Computer Science and Information Engineering
※Research Interests: Computer Systems, System Software, Cloud Computing, Simulation and Performance Evaluation